Not sure how much truth is in this …
This is a real threat for the shipping industry. Remember Maersk that earlier had to reinstall 4000 servers and 45000 PC’s because of the NonPetya ransomware? I am afraid that there is not much awareness about this phenomenon in our industry which can attract the attention of hackers who are always looking for easy targets. They are like thieves who prefer to visit houses with open windows and easy locks, same principle.
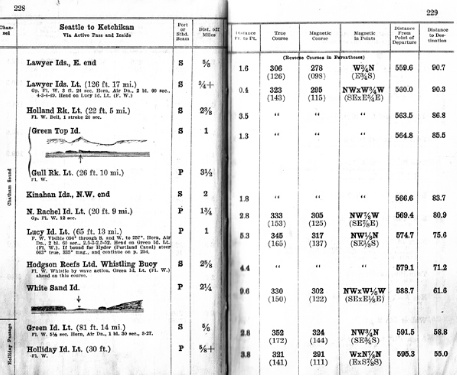
Particularly a problem for ECDIS since antivirus software is not usually installed with ECDIS.
Securing dedicated ECDIS platforms should not be too difficult. Computing platforms with a singular purpose can be pretty well isolated from the network without impacting their functionality in the same way as in general computing. You essentially need only navigational network data and a chart update deployment vector, and for the rest the system can be sealed off tight. There is no need to run anything with administrator permissions, and admin creds can be kept by shoreside technical personnel. You don’t need to include system administration functionality in the standard operating interface either, so the system can even be made somewhat secure against social engineering.
Sometimes software updates maybe necessary which require an internet connection. Care should be taken to insure that safe server identity is established. For the rest, stay away from the internet and put a ban on the use of USB sticks which can be the source of all kind of infections. For servers there are possibilities to create a Group Policy to enable and disable USB ports and for Windows versions changes in the registry can establish the same. Here is an example for Windows 7
If USBs are not used, how are the charts and software updated?
Since most charts are licensed at high fees for discrete areas and limited times, charts may need to be added for every voyage, as well as updated.
Keeping USBs clean and never using the wrong one is not as easy as it sounds.
How do we know that viruses cannot enter the system via power supply wiring? Or through GPS or AIS connections.
Most importantly, it’s just a question of when, not if, the chart vendors will be hacked, and malware inserted.
Just saw a TV show where NSA computers were hacked by a phone being used to reprogram the video card in a computer terminal.
Whatever can be imagined , can eventually be done.
There are too many super bright creative people with state intelligence service resources supporting them to find ways to cause mischief. We know they can spoof GPS signals, so we can be sure they are going after ECDIS too.
For instance a station with an enabled USB port could be locked with a physical USB port blocker. And yes, you cannot make it 100% safe but the idea is to make it as difficult as possible for intruders.
Probably, the weakest point is the internet connected computer used to download the charts to a USB. That computer can infect the USB, No matter how good the virus detection and blocking software on that computer, some new malware could get through, or it may not get used correctly every time. More likely, is accidental use of the wrong USB.
It seems to me that ECDIS needs more powerful computers with good virus and malware protection. It also seems to me that critical systems, like ECDIS, should have a different operating system that is less susceptible to viruses and malware. Most malware and viruses target the Windows operating system.
The ECDIS is definitely vulnerable, Transas is running on Windows, but how vulnerable depends on how it’s set up.
Originally we had to download charts and updated via email, had to use USB drive. Used a dedicated USB for the ECDIS but access to the email computer on the bridge not so tightly controlled.
Once our sat system got upgraded so that we had internet access the ECDIS was connected directly so all interactions with the shoreside server was direct through the ECDIS. Far better setup.
By far the worse offenders of computer security are the know-it-all computer guys.
Transas is one on the most popular ECDIS systems. It is a Russian owned, developed, and controlled product. This means that it is ultimately controlled by the Russian government. It undoubtedly has backdoors built into it. I hear that MSC is removing Transas ECDIS units for this reason.
Transas is now part of Wartsila. It was started in Russia 1990, but the HQ moved to UK already in 1991 and now operate worldwide, using technology from wherever it can be had, incl. USA:
https://www.marinemec.com/news/view,transas-makes-a-historic-transition_51150.htm
Maybe CIA sneak in some backdoor in whatever software or components in Transas equipment made in USA??
Virus can come from any number of sources. When I was involved in a newbuilding program the technician’s laptop that was used to load the VDR software was infected. Fortunately for us our IT guy was there setting up the ship’s server and computer network. He saw something screwing going on and was able to isolate and ultimately remove it.
Yeahhhhh. That works great until an idiot tech who shall remain nameless plugs in his USB drive to do an update and infects all 10+ networked ECDIS stations on a subsea construction vessel based out of Fourchon with a nasty virus. ![]()
I am thinking in terms of a terrorist attack.
Hack the control systems and take over just when entering port.
Suddenly apply full power and sharp turn into the putty and hey presto… you have closed a major port.
IMO and class flag state is so far behind re computers.
It was going to happen as all the retired old farts are in senior positions in those organizations.
Not to mention doing HSEQ in your office
Its bad enough in the DP world, now the bridge is covered in computers that need updates, scary.
Automation and power management for the most part is being designed as its being installed on board.
Or its classed but due to issues the software supplier keeps changing it, where does class stand in that?
PC’s and Ethernet controlled thrusters, scary sh1T.
none of that would ever be considered on aircraft, there’s a hint.
You could use windows embedded version, that would be a start if the IMO demanded that.
I think that critical systems computers , such as ECDIS, should: run on a limited access computer chip using a limited access machine code, run a limited access non-windows operating system, only accept special USBs and computer connections.
A new approach to charts and chart corrections is needed. All ECDIS units should come with pre-installed worldwide charts. 95% of chart updates should be done only once per year, and only, on special USBs. A rare few other interim updates might be needed. The surface of the earth where ships normally trade is reasonably well charted, and physical features do not change at all in most places. In this era of electronics, physical aids to navigation are much less important than they use to be. There are too many minor changes to nav aids that are not necessary; this should be greatly reduced, which would reduce the need for updates.
Doing weekly chart corrections is crazy and creates too many opportunities for infection and operator errors. It’s also far too expensive and time consuming for very little actual practical benefit. Doing monthly electronic updates to the publications would be more than enough.
Losing email is a lot bigger problem for me the losing the ECDIS. Without email doing the pre-arrival paperwork becomes very difficult or impossible. When the ECDIS fails I just need the tech waiting in the arrival port.
I suppose if the navigation was difficult… If the arrival port was SIngapore eastbound I might anchor off Port Klang and have the tech come out by boat.
As far as paper charts go, general area paper charts should still be carried as a “for reference only” emergency back up, but that corrections should not be required.
I have a windows laptop with Rosepoint and an iPad with iSailor (Transas). Two completely different operatining systems, computer chips, and chart plotter products, each with its own GPS. I am not dependent upon ship’s equipment. I’m prepared to do without it.
That’s why email is critical. A chart is nothing but navigation information in graphical form. For navigation the information is what is needed, not the chart itself.
Information can be in many forms, a chart made on board with info from the pubs, a chartlet scanned and sent to the ships, a chart brought out by a pilot, the pilot himself, info from a pilot via vhf ect…
It’d be tough getting to Singapore eastbound without a chart but getting to Port Klang, for example, could be done with the info in some other form.
all good but hasnt fixed our issue that there are PC’s on the bridge and maybe running your engine room as well and the IMO/class/Flag state cant deal with them yet